Difference between revisions of "201801 Consumer Centered Data Exchange"
Aaron Seib (talk | contribs) |
Aaron Seib (talk | contribs) |
||
| Line 78: | Line 78: | ||
Description of Transactions | Description of Transactions | ||
| − | 0 – OAuth Ceremony where Consumer interacts with OAuth flow to convey their sharing preferences | + | :0 – OAuth Ceremony where Consumer interacts with OAuth flow to convey their sharing preferences |
| − | 0’ – Saving of rules into FHIR Consent resource | + | :0’ – Saving of rules into FHIR Consent resource |
| − | 1 – Request by App for authorization to access specific data (scope) at Resource Service (target) resulting in an authorization (token+scope) | + | :1 – Request by App for authorization to access specific data (scope) at Resource Service (target) resulting in an authorization (token+scope) |
| − | 2 – Request by App for access to data given token+scope | + | :2 – Request by App for access to data given token+scope |
Revision as of 19:14, 5 December 2017
Track Name
Consumer Centered Data Exchange (CCDE)
Submitting WG/Project/Implementer Group
FHIR Project Director, in association with the National Association For Trusted Exchange (NATE)
Justification
The justification for this track is to continue to develop an understanding of what the main specification of the US core IG should say about enabling consumer-centric use case. This will be the second CCDE connectathon. The inaugural connectathon spurred significant interest and participation in San Diego followed by voluminous post-connectathon discussion.
The participants of the January event aggregated around two use cases:
Scenario 1) Consumer Access enabled by OAuth from a consumer controlled application – there is ambiguity in the community regarding the use of the FHIR standards to properly record when consumer access is enabled via OAuth. Striking the appropriate balance between minimizing the level of effort on the part of the consumer with the data holder's requirement to maintain an accounting of disclosures for audit and reporting purposes requires further deliberation to determine what if any modification to existing standards are needed and to provide guidance to aid developers implementing this use case in their systems. We aim to explore the various implementation considerations, doing so in a policy transparent way.
- A consumer, such as a medicare beneficiary, wishes to authorize the sharing of their health information from a Data Provider, such as CMS, with a consumer controlled app of their choice; Data Provider wishes to generate required information to capture the consumer's authorization and all necessary information to be able to report an complete accounting of disclosure.
Scenario 2) Consumer Initiated Exchange - incorporating privacy preferences when sharing 'on behalf of' the consumer in addition to the requirement to be able to account for disclosures under HIPAA in the US, data holders are obligated to be able to share data with other entities 'on behalf of the consumer'. A number of elements are being brought to bare to address this complex requirement that intersects numerous regulatory and technical challenges including Cascading OAuth, UMA, Security Labeling Services, a FHIR-based eConsent portals and electronic Consent Management Systems. The goal of this scenario to examine how these components can empower consumers to communicate their privacy preferences to data holders who share information with covered entities on their behalf. We aim to explore the various implementation considerations, doing so in a policy transparent way.
- A consumer, such as a patient being treated by a Provider Participating in an HIE, wishes to authorize the HIE to share their health information with other providers attributed to them in the HIE. Data is shared, on-behalf of the consumer between their providers on the network without the consumer necessarily receiving a copy of the record themselves.
The affinity to these use cases were observed to be based on the architectures being employed by the participants of each use case but an important observation that has been made is that the underlying resources and gap in the standard (specifically around standard Scopes) was common across the two groups. The goal of this connectathon will be to more purposely explore the commonalities between the use cases and determine how the different architectures employed bare on the existing standards and to begin to explore the elucidation of standard Scopes that would be common to both.
Prior Connectathon track 201709 Consumer Centered Data Exchange
Relevant background
- HL7 blog - HL7 FHIR Connectathon 16: Patient Consent Forms: Redundant in the world of OAuth2? Part 1 of 2
- HL7 blog - HL7 FHIR Connectathon 16: Patient Consent Forms: Redundant in the world of OAuth2? Part 2 of 2
- John Moehrke blog - Remedial FHIR Consent Enforcement - note this is a different model than this track is following, but was used for alternative track.
- Grahame/Josh blog - Sharing Information with a Patient Case Manager
email discussion list
- mailto privacyconsent@lists.hl7.org
- archive of discussion
- signup at http://www.hl7.org/myhl7/managelistservs.cfm
- You do not need to be an HL7 member to signup for mailing lists
Proposed Track Lead
Aaron Seib
Expected participants
- NATE
- John Moehrke (HL7 Security co-chair) SME on FHIR Consent
- http://test.fhir.org/r3
- HSS IDEA Lab Authors of the POET specification Mark Scrimshire & Alan Viars
(others: email aaron.seib@nate-trust.org if you are interested in getting involved)
Architectures
Both Architectures involve the following Actors:
Consumer - Gives ceremony instantiating authorization rules for an end-point (Consumer Controlled App in the case of the Consumer Access scenario); designated end-points in the Consumer Initiated Use Case) access to the resource service managed data [Patient who provides their privacy preferences - via the OAuth interaction in the Consumer Access scenario; via the Consent Service in the Consumer Initiated scenario]
Authorization Service - makes authorization decisions on how an end-point access to specific data at specific Resource Service(s) according to rules (Privacy Preferences indicated by the Consumer)
Resource Service - holds data that is controlled by Consumer's Privacy Preferences (Such as an EMR, an HIE or a Payer)
End-point - the "Application" (including a Consumer App; a 3rd Party end-point indicated by the Consumer such as their PCP's EMR or their Payer's care management team; a Research Repository; etc.) that is given rights to access data on a Resource Service at the direction of the Patient.
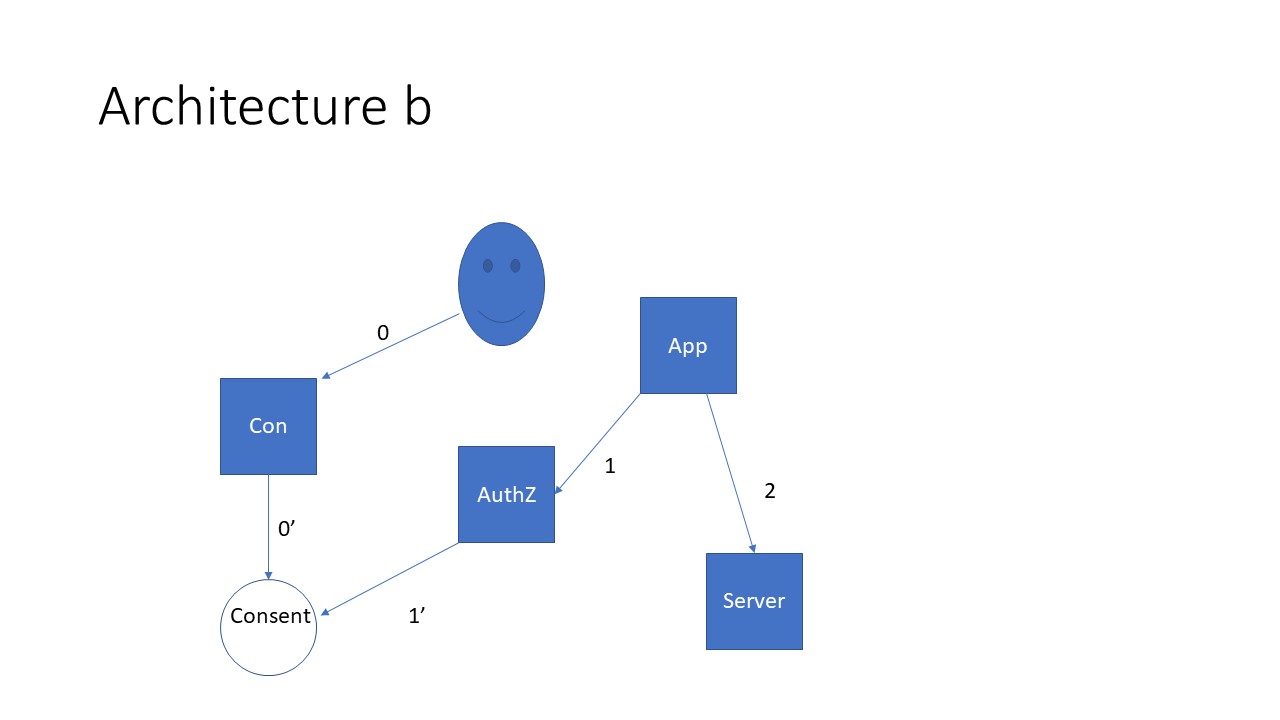
The Consumer Initiated Scenario involves the Consent Service actor.
Consent Service - a stand alone UI that captures the privacy preferences of the Consumer (which performs a similar function to the SMART OAuth interaction where the consumer indicates their privacy preferences interactively with the Authorization Service)
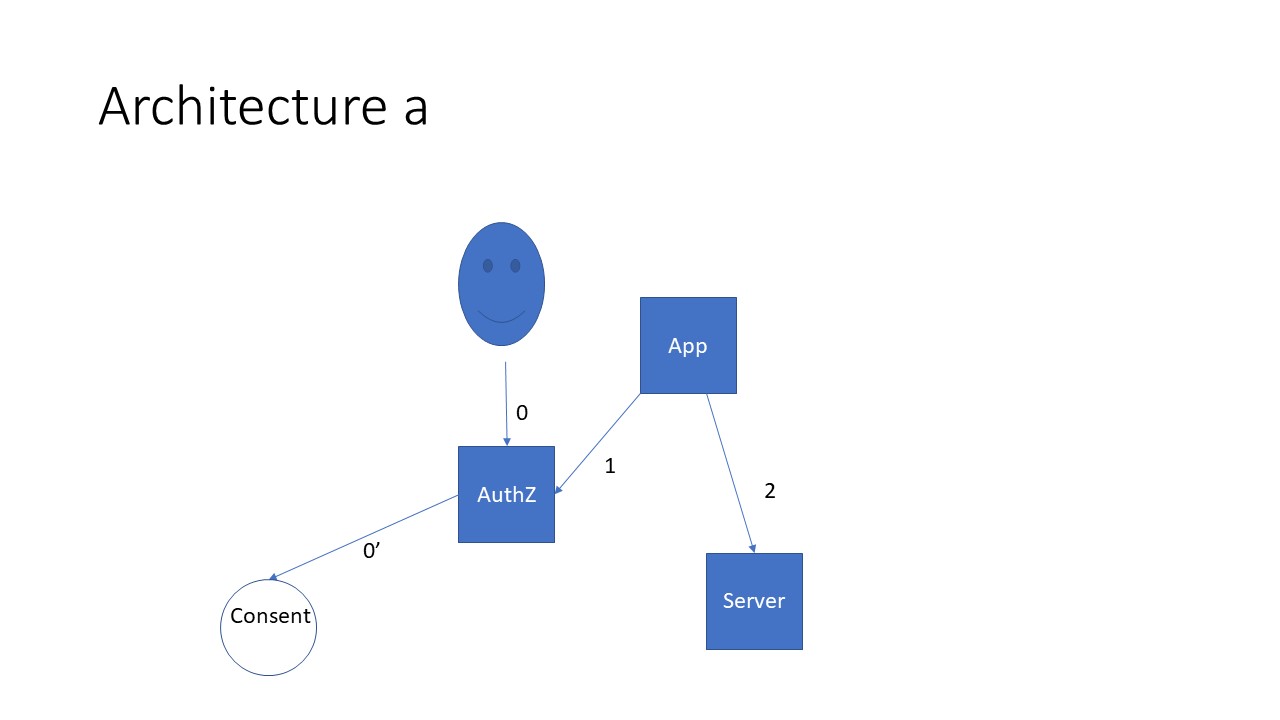
Architecture 1) Consumer Access via OAuth
- Action: Consumer Authorizes the sharing of their Health Information with an App of their choice using the SMART OAuth pattern to authenticate
- Precondition: Consumer App is registered with the disclosing system (any FHIR based system that holds PHI about the consumer such as an EMR or Payer)
- Success Criteria: Without any special effort of the part of the consumer the disclosing system retains all required information to satisfy regulatory and audit requirements
- Bonus point: Being able to handle a consumer's rescinding of their authorization to disclose
Description of Transactions
- 0 – OAuth Ceremony where Consumer interacts with OAuth flow to convey their sharing preferences
- 0’ – Saving of rules into FHIR Consent resource
- 1 – Request by App for authorization to access specific data (scope) at Resource Service (target) resulting in an authorization (token+scope)
- 2 – Request by App for access to data given token+scope
Architecture 2) Consumer Initiated Exchange - sharing 'on behalf of'
- Action: Via a user friendly interface a consumer captures their privacy preferences in a computable way
- Precondition: Data holders are subscribed to the services that enable the capture of the consumer's privacy preferences and can electronically share with end-points indicated by the consumer.
- Success Criteria: The designated recipient that the data holder is disclosing to on behalf of the consumer receive all data except that which the consumer's privacy preferences indicate should not be shared it.
- Bonus point: Demonstrate how the solution set will allow the recreation of the consumer's privacy preferences at any point in time in the past following one or more changes in preference settings.